Users can stop fake McAfee pop-ups by immediately closing suspicious browser notifications using Alt+F4, clearing browser cache and cookies, and disabling notifications from unverified websites. Legitimate McAfee alerts only come through installed software, not browsers, making browser-based warnings inherently suspicious. Crucial protective steps include running malware scans, removing suspicious extensions, and keeping system software updated. Additional security measures can provide thorough protection against these deceptive tactics.
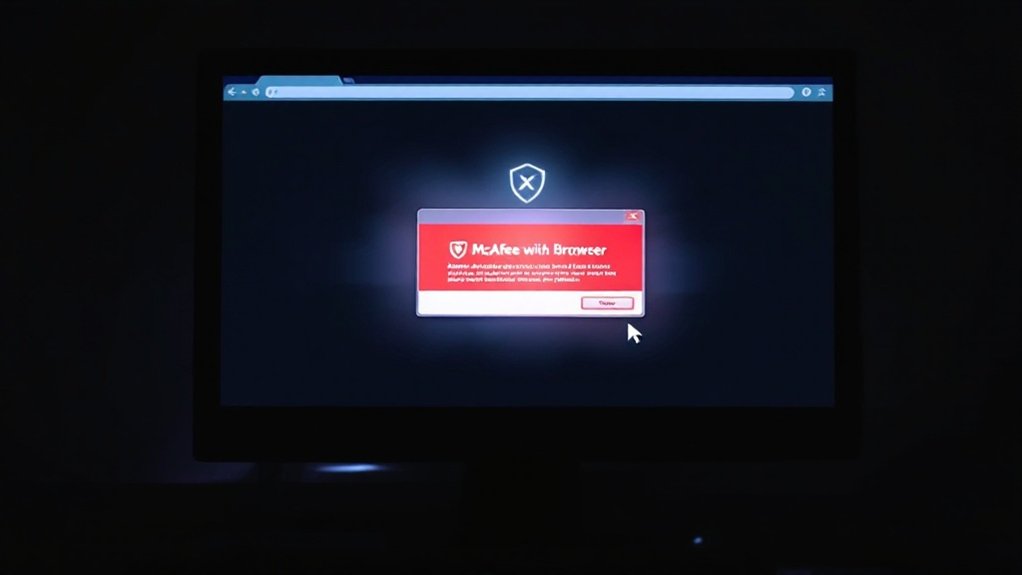
The proliferation of fake McAfee pop-ups has become an increasingly concerning security threat for internet users worldwide. These deceptive notifications, often appearing through web browsers rather than legitimate security software, employ fear tactics and urgent language to manipulate users into revealing personal information or making unnecessary payments. The scammers specifically target users by showing alerts about expiring subscriptions, despite no McAfee software being installed. Malicious downloads can sneak in through pirated software and compromise system security.
Security experts highlight that genuine McAfee alerts exclusively originate from within the installed application, not through browser-based notifications. Users encountering these fraudulent pop-ups should immediately close their browsers using Alt+F4 or Task Manager, followed by a thorough clearing of browser cache and cookies. In persistent cases, completely resetting browser settings to default configurations or performing a clean reinstallation may be necessary.
Legitimate McAfee notifications come solely from installed software, never through browsers. Close suspicious pop-ups immediately and clear browser data thoroughly.
Moreover, users should review and disable browser notifications, particularly from suspicious websites, whilst maintaining strict control over notification permissions through browser settings. A thorough security approach involves removing suspicious browser extensions and recently installed applications that could be responsible for generating malicious pop-ups. Installing phishing detection tools like those offered by Norton can provide an additional layer of defense against fraudulent pop-ups.
Regular malware scans can detect potentially unwanted programs, whilst keeping all software updated helps prevent security vulnerabilities. Browser security settings should be optimized by enabling pop-up blockers, activating safe browsing features, and utilizing built-in privacy protection tools.
System-wide protection measures play a significant role in preventing fake security notifications. This includes maintaining legitimate antivirus software, enabling Windows Defender on Windows systems, and implementing reliable ad-blocking solutions.
Security professionals recommend using a Virtual Private Network (VPN) for further protection against malicious actors attempting to exploit system vulnerabilities. Safe browsing practices remain vital in preventing exposure to fake McAfee pop-ups.
Users should exercise caution when encountering website notification requests, verify security warnings through official channels, and maintain strong, unique passwords across all accounts. Regular data backups provide an additional layer of protection against potential malware attacks, ensuring critical information remains secure regardless of whether systems become compromised.
Frequently Asked Questions
Why Do Fake Mcafee Pop-Ups Specifically Target Windows Users?
Fake McAfee pop-ups primarily target Windows users because of the operating system’s dominant 75% market share and its large base of less technically sophisticated users.
Windows’ architecture, which allows deeper system access, combined with users’ tendency to trust security-related alerts, makes it an ideal target.
Moreover, Windows users’ familiarity with McAfee as a legitimate security brand increases the likelihood of successful social engineering attempts.
Can Fake Mcafee Pop-Ups Steal My Saved Passwords?
Fake McAfee pop-ups can certainly compromise saved passwords through multiple attack vectors.
These malicious notifications often contain scripts that harvest credentials stored in browsers, whereas accompanying malware may include keyloggers that record login information.
Security experts warn that clicking these pop-ups can redirect users to phishing sites designed to steal passwords, and downloaded trojans can systematically extract saved credentials from browser databases, password managers, and system files.
Will Resetting My Browser Completely Prevent Future Fake Mcafee Pop-Ups?
Browser resets can greatly reduce fake security pop-ups but cannot guarantee complete prevention of future incidents.
Although resetting clears malicious scripts and removes compromised settings, sophisticated scammers continually develop new tactics to bypass browser security.
Users must combine reset procedures with ongoing security measures, including updated antivirus software, ad-blockers, and proper browsing habits, to maintain long-term protection against deceptive pop-ups and similar threats.
Do Fake Mcafee Pop-Ups Appear on Mobile Devices Too?
Fake McAfee pop-ups frequently appear on both Android and iOS mobile devices through various delivery methods, including compromised websites, malicious ads, and deceptive push notifications.
Mobile browsers’ limited security features and smaller screens make smartphones particularly vulnerable to these scams. The pop-ups often exploit mobile-specific characteristics, such as touch interfaces and notification systems, during mimicking legitimate system alerts or application messages to deceive users.
Should I Report Fake Mcafee Pop-Ups to the Real Mcafee Company?
Reporting fake McAfee pop-ups to the legitimate company is strongly recommended by cybersecurity experts, as it helps track emerging threats and improve security measures.
Users can submit reports through McAfee’s official website, including screenshots and detailed information about the encountered pop-up.
This data allows McAfee to analyze patterns, develop countermeasures, and warn other users about specific scams, contributing to broader cybersecurity protection efforts.









