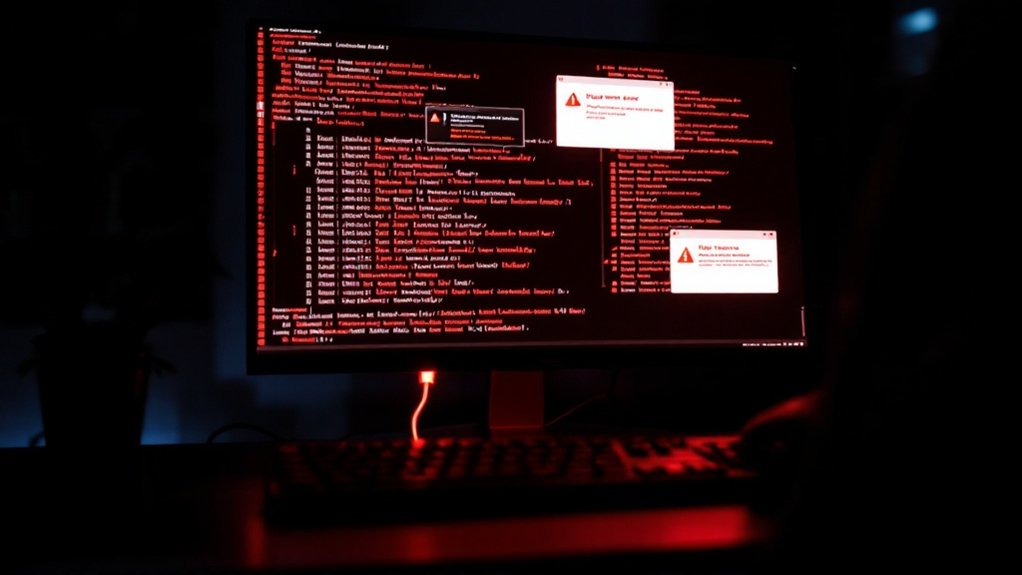
Security experts identify several key indicators of computer compromise, including persistent pop-up advertisements, unexpected system slowdowns, disabled security features, and unauthorized login attempts from unknown locations. Common warning signs involve unusual spikes in CPU usage, missing files or folders, automated social media posts, and modifications to browser settings without user consent. Network anomalies, such as increased data usage and blacklisted IP addresses, in addition suggest potential system intrusion. Understanding these warning signs allows users to detect and respond to security breaches effectively.

In the domain of cybersecurity threats, identifying whether a computer has been compromised remains a critical concern for both individuals and organizations. The presence of unusual pop-ups and advertisements often serves as an initial indicator of system compromise, particularly when these intrusive elements persist even after closing web browsers or appear directly on the desktop interface, frequently promoting questionable services or displaying fake security warnings. Missing files and folders can also indicate unauthorized system access.
System performance degradation frequently accompanies malicious infiltrations, manifesting through extended startup times, unexpected program launches, and abnormal spikes in CPU or memory usage visible within Task Manager. These performance issues often coincide with the appearance of suspicious programs, unauthorized modifications to browser settings, and the installation of unwanted toolbars or extensions that resist normal removal procedures. Two-factor authentication provides an additional layer of security against unauthorized system access.
Malware infiltration often reveals itself through sluggish performance, intrusive programs, and browser modifications that stubbornly resist standard removal methods.
Compromised systems frequently exhibit signs of unauthorized access to user accounts, including unexpected password reset notifications, login attempts from unknown locations, and unauthorized financial transactions. Regular data backups to cloud storage can help mitigate potential losses from such security breaches.
In many cases, victims uncover their social media accounts sending automated messages to contacts without their knowledge, at the same time finding themselves locked out of their own accounts because of altered credentials.
Security mechanisms often become primary targets, with attackers attempting to disable or modify critical protective features. Users may find their antivirus software unexpectedly deactivated, firewall settings altered, or system restore points eliminated, effectively hampering recovery options. These modifications typically accompany more severe symptoms, such as ransomware infections that encrypt valuable data and demand payment for restoration.
Network behavior analysis reveals additional warning signs through unexpected increases in data usage, blacklisted IP addresses, and unauthorized modifications to router configurations.
Users might notice their internet connection becoming erratic or uncover unfamiliar devices connected to their network. These indicators, combined with the presence of encrypted files bearing unusual extensions and the inability to access common file types, strongly suggest system compromise requiring immediate professional intervention and security measure implementation.
Frequently Asked Questions
Can Hackers Access My Computer Even When It’s Turned Off?
Although computers are typically secure when powered off, certain vulnerabilities remain. Wake-on-LAN features can allow remote activation, and sophisticated firmware exploits may compromise systems even when shut down.
Physical access presents risks for hardware tampering, as standby modes can unexpectedly wake devices. Air-gapped systems, though disconnected from networks, remain susceptible to specialized attacks through electromagnetic signals, acoustic methods, or compromised peripherals.
How Often Should I Change My Passwords to Prevent Hacking?
Modern cybersecurity guidelines recommend changing passwords only when necessary rather than on a fixed schedule.
NIST (National Institute of Standards and Technology) advises annual password changes or immediate updates following security breaches. Users should create strong, unique passwords for each account and implement them quickly after data breaches, suspicious account activity, or device compromise.
Password managers and two-factor authentication provide additional security layers as well as eliminating the need for frequent, arbitrary changes.
What Should I Do Immediately After Discovering My Computer Is Hacked?
Upon uncovering a computer hack, immediate disconnection from all networks is crucial, followed by removal of external storage devices to prevent further data compromise.
Using an uncompromised device, users should change passwords for critical accounts, particularly email and financial services, at the same time enabling two-factor authentication.
A thorough security scan using updated antivirus software must be performed, followed by systematic monitoring of accounts for unauthorized activities and suspicious transactions.
Are Apple Computers Less Likely to Get Hacked Than Windows PCS?
Statistical evidence indicates that Apple computers typically face fewer cybersecurity threats than Windows PCs, primarily because of their Unix-based architecture and smaller market share.
Nevertheless, Mac-targeted malware is increasing at twice the rate of Windows threats in recent years.
Although Macs benefit from built-in security features like Gatekeeper and XProtect, neither platform is immune to attacks, and both require vigilant security practices.
Can Someone Hack My Computer Through My Printer or Other Peripherals?
Peripheral devices pose significant security risks as potential entry points for hackers. Network printers, USB hubs, wireless keyboards, and other connected devices often contain vulnerabilities in their firmware that malicious actors can exploit.
Security researchers have demonstrated that compromised peripherals can be used to install malware, capture keystrokes, or gain unauthorized system access. Even seemingly innocent devices like SATA cables can be manipulated to exfiltrate data through electromagnetic emissions.